Having spent a lot of time over the last few years presenting on the ransomware landscape and attack mitigation, I’m really excited by what Pure is announcing – a unique ability to mitigate the impact of ransomware attacks.
Simply put, Pure is now offering an industry-unique combination of Immutability Plus, simplicity, and high speed restore which can have a powerful impact on your ability to recover from ransomware attacks. This is possible due to FlashBlade™, Pure’s purpose-built file and object platform that natively scales out and is built for throughput. So, what’s new? Immutability Plus via FlashBlade SafeMode is the key. This offers the ability to prevent backups stored on FlashBlade from being compromised by attackers, thus acting as a force multiplier on FlashBlade’s existing simplicity and Rapid Restore capability.
I realize that’s a big claim – so let’s back up a bit first:
Constant & Increasing Attacks – Why?
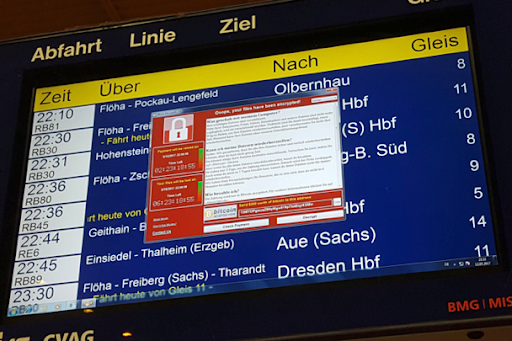
If you’re reading this, you already know that ransomware attacks are a daily occurrence. I don’t want to quote scary statistics – they’re just a Google News search away after all. One image has stuck with me over the years though – WannaCry on a Deutsche Bahn train schedule screen. Call it the equivalent of a Windows blue screen of death in an airport, but far worse.
From an economic impact, the numbers almost defy belief – a 479x increase in the economic impact of ransomware  between 2015 and 2019 (per ZDNet and TechRepublic). Even as the exact numbers may be hard to pin down, we are looking at more than two orders of magnitude.
between 2015 and 2019 (per ZDNet and TechRepublic). Even as the exact numbers may be hard to pin down, we are looking at more than two orders of magnitude.
Given this dramatic growth in the ransomware threat, it’s reasonable to ask why the industry hasn’t been able to get a handle on this issue. In discussions and research, I see several main issues.
- Asymmetry of attack cost vs. value extracted – there are real economic factors at play. Simply put, it is cheap for the attackers to keep attacking, and expensive for the victims – a very simple cost/benefit analysis for attackers.
- Complexity of the modern IT stack – the modern IT datacenter stack has so many things to keep updated, patched, and hardened. This is also known as “an insane number of attack vectors.”
- Payment methods – continuing successful use of Bitcoin or other cryptocurrencies to provide relatively reliable, relatively anonymous payment methods.
- Ransomware-as-a-Service kits – now available for those who know where to look online. Attackers can purchase kits with a range of technical skill needed, encryption types used, and more.
In the “dark humor” category, I’ve also heard ransomware attacks defined as “a problem requiring an unplanned restore of massive amounts of data from products designed for yesterday’s problems.” Imagine a concurrent Disaster Recovery of your production AND backup systems.
How to Defend
As with many security conversations, Defense in Depth is required. Here are the main categories of defenses I cover when presenting on this topic.
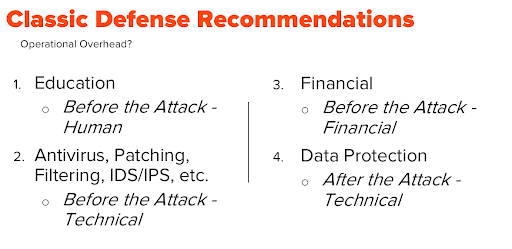
What complicates this are the many options in each category, especially #2. There are so many possible attack vectors to technically defend against that maintaining them from an operational perspective can be overwhelming.
Note: while not the focus of this blog, FlashBlade can dramatically accelerate and simplify Splunk environments and Splunk can assist with ransomware attack detection and defense. See below for links.
However, truly determined attackers often weave their way through any multi-layered defense. In this event, backups then become the defense of last resort. This isn’t hard in theory – we all know backups are critical from many trusted online sources. For instance, the US Department of Health and Human Services admonishes hospitals that…
Easy in Theory, Hard in Practice
So why do customers end up paying ransoms if it’s as theoretically simple as restoring from backup? I think we all know the first part of the answer – often backups don’t work effectively or quickly when you need them most. Daily backup failures are almost a rite of passage for junior admins to track down each and every day.
When it relates to ransomware, however, the impact of failed backups, corrupted backup data, or slow restores become much higher. This leads us into the idea of a High Impact, Low Probability event and the best way to protect against it.

A system that is highly complex and requires daily care and feeding (e.g. tape drives for backup) will more than likely not be ready when a High Impact, Low Probability event occurs. From an IT perspective, there are daily issues to keep systems running. While ransomware is a constant and growing threat, ransomware recovery is not a daily item (Low Probability) compared to all the daily tasks needed to keep the datacenter lights on. This is where simplicity comes to the forefront.
Even if your backups are running successfully, we are now seeing ransomware attacks that target both backup data+backup catalogs and even storage array snapshots. This is the definition of a very, very bad day.
Given we’re pushing the lengths of a blog post, stay tuned for part two of this post. In the meantime, see how you can protect against ransomware attacks and how Pure FlashBlade can help.
See more about Pure and Ransomware:
- Webinar: Protect Ransomware’s Next Target – Backups
- FlashBlade can dramatically accelerate & simplify Splunk environments
- Splunk can assist with ransomware attack detection and defense