前回の「今さら聞けないフラッシュって?― 第 1 回」では、フラッシュメモリの概要について触れました。第 2 回の今回は、エンタープライズ向けのストレージでフラッシュを利用する際の一般的な懸念事項を挙げてみようと思います。
一般的に、SSD に対する不安点として以下のような事柄をよく聞きます。
- 書き込み寿命がある
- GB 単価が高い
- 書き込み処理が苦手
これらについて、1 つずつ解説します。
1.書き込み寿命がある
SSD は HDD より寿命が長いと言われています。 もちろん寿命は使用時間(連続稼働時間)などにも関係していますが、特に書き込み回数に影響されます。前回も触れましたが、SSD には書き換え数の上限があります。
| ビット数/セル | 1 | 2 | 2 | 3 | 3 |
| 書き換え回数(概数) | 100万回 | 1万回 | 3,000回 | 1,000回 | 3,500回 |
| コスト/GB | $$$$$ | $$$$ | $$$ | $$ | $ |
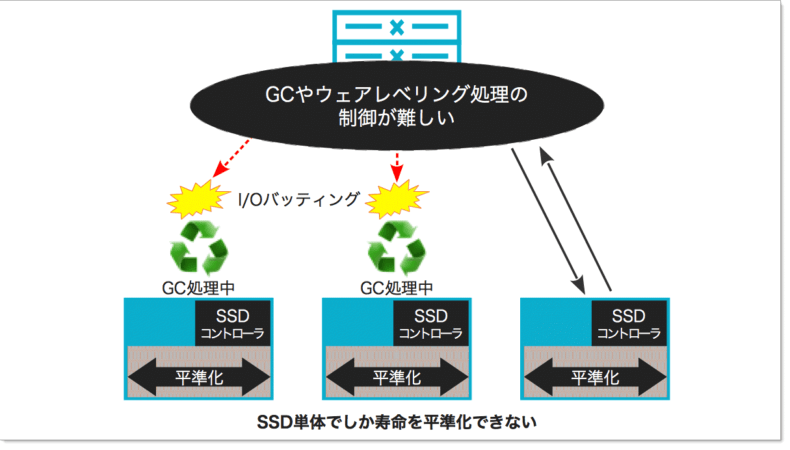
書き換え限度回数が存在する媒体においては、その使用寿命を延ばすため、書き込む場所が集中しないように平準化を行う「ウェアレベリング」という手法が用いられます。ただし、一般的なオールフラッシュストレージでは、ウェアレベリングは SSD コントローラにより処理されるため、SSD 単体でしか書き込み回数を平準化できません。

また、後述の「書き込み処理が苦手」にも関係しますが、書き込み中に読み込み処理などの I/O がバッティングした際、遅延が一気に上昇してしまいます。上図の構成では SSD コントローラが各 SSD 単位で I/O を分散することになります。
2.GB 単価が高い
NAND フラッシュの大容量化とそれに伴う容量単価の下落で、普及期を迎えたフラッシュですが、前述の表のとおり、コンシューマ向けとエンタープライズ向けでは、耐久度(書き換え回数)に比例して GB 単価に大きな差が生じます。例えば、エンタープライズ向けの SLC を選択した場合には、製品コストに大きな影響が出ます。
3.書き込み処理が苦手
フラッシュは書き込みが苦手なデバイスであると言われます。前回の「SSDとは?」のセクションで SSD の構造を見ていただきましたが、フラッシュの場合、1 ビットずつディスクに書き込んでいく磁気ディスクとは異なり、読み・書きは「ページ」単位、削除は「ブロック」単位で行われます。ここで、書き込み処理が苦手とされるデータの上書きが行われる際の動きを見てみましょう。

上図に示すように、データを上書きする場合には、ブロック単位でデータを一旦退避して該当ブロック上のデータを消去し、データを書き戻すという処理が発生します。ワーストケースでは、例えば 1 MB のブロックに対して 4 KB のデータを上書きするのに、1 MB の書き込みが発生してしまいます。I/O 処理が多くなると、その分フラッシュメディアの劣化にもつながります。
特に、SSD が使い込まれた状態の場合では、上記のように SSD 内部でデータを退避させて、入れ替えながら書き込みを実施する動作が頻繁に行われるため、無駄な書き込みが増え、性能が不安定になる原因となります。
つまり、従来型ストレージのように 4 KB 単位でフラッシュメディアに書き込みを行った場合には、非常に非効率な書き込みとなり、性能や書き込み寿命に大きな影響を及ぼしてしまいます。

以上のように、SSD は HDD に比べて非常に高速である一方、留意すべき点もあります。次回は、FlashArray がどのようにこれらの課題を解決し、お客様にとって使いやすく、壊れにくいストレージを提供しているかについてご紹介いたします。
The Digital Operational Resilience Act (DORA) came into effect on January 17, 2025, with extensive guidelines and a detailed regulatory framework for how all financial services entities doing business in the European Union ensure data resilience against unplanned disruptions. It also recognizes a reality broadly accepted by cybersecurity professionals that it is no longer a question of if a cyberattack occurs, but when. This crucial EU legislation brings a new level of rigor and accountability to the financial services industry that will continue to evolve to safeguard the stability of the EU and global financial ecosystem.
Many sectors of the financial services industry beyond traditional banks and credit institutions now fall under DORA regulations, including payment providers, investment firms, trading venues, insurance providers, and third-party information and communication technology (ICT) service providers. Sectors that are new to this level of regulation may struggle to comply as indicated by European financial regulators’ DORA “Dry Run exercise.¹” They will also likely face additional scrutiny by interconnected customers, partners, and other stakeholders as a new operational risk. Non-compliance no longer means just the potential for a very large fine but also reputational damage and liability for a company, its directors, and its partners.
While it remains to be seen how quickly financial regulators act, DORA represents a shift from guidelines for data readiness and cyber resilience to enforcement of it. Given the expansive nature of DORA, which significantly broadens the EU’s financial regulation of information technology, European financial regulators, lacking unlimited expertise and resources, may face challenges enforcing all aspects of DORA immediately. As a result, regulators are likely to adopt a targeted approach, focusing on the most critical and visible areas of noncompliance.²
ランサムウェア対策ガイド – 攻撃の予防と復旧

What Financial Organizations Are Prioritizing
One of the top priorities for DORA compliance is the submission of accurate and technically compliant registers of information. Financial regulators have emphasized that registers will be a primary focus of enforcement, and they expect organizations to submit them early in 2025. Submitting an accurate register that details the organization’s most significant IT providers may be more beneficial than submitting incomplete information about all of its IT providers.
For data protection leaders and CIOs, DORA is a call to action to examine legacy systems and consider whether they are capable of withstanding today’s cyber threats and can deliver the performance required for efficient, rapid service recovery. Beyond identifying and mapping key systems, applications, and workloads with respective ICT providers, organizations should carefully consider the core capabilities that protect, defend, and recover these systems. Critical capabilities include:
- Data protection and cyber recovery: Rapid recovery capabilities are essential under DORA as a way to minimize the operational impact of an attack. For critical systems (e.g., payments), the only way to achieve the most stringent, ultra-short recovery time objectives required by operational resilience regulations is to recover using storage-based immutable snapshots. These snapshots should be securely stored in an isolated (or virtually air-gapped) repository.
- Early-warning threat detection: Identifying and remediating potential cyber threats earlier is an important aspect of data protection and readiness. The capability to continuously scan data to detect anomalies and identify threats like ransomware and malware in real time and automate remediation is essential for faster containment of an attack.
- Isolated recovery environments (IRE) or cleanrooms for resilience testing: Establishing a completely self-contained, isolated recovery environment where data can be restored for forensic and application analysis and validated as clean before returning to production speeds recovery. IREs also allow organizations to continuously test and improve cyber recovery practices for organizational readiness.
- Scalability and performance: Businesses will continue to evolve their services, face new regulatory requirements, and deal with emerging cyber threats. It’s important to consider a solution’s ability to scale as data requirements change across distributed, hybrid environments while maintaining high-performance speeds for data protection and recovery.
Compliance with Confidence
Organizations that delay establishing robust capabilities to meet DORA and other evolving resilience regulations, such as PSD2, NIS2, APRA CPS 230, and the European Cyber Resilience Act coming into effect in 2026, may find themselves with mounting challenges to overcome. They may also find themselves at a competitive disadvantage to firms that can demonstrate their ability to remain resilient in the face of disruptions in the global financial ecosystem. Working with partners who understand the regulation’s resilience requirements and deploying robust solutions can help organizations ensure they are compliant and better prepared to meet new regulatory challenges and defend their data environment against emerging threats.
Pure Storage and Commvault have come together to build a joint solution, modular in design, that helps financial institutions enhance their cyber resilience practices and address key pillars of DORA for incident response and resilience testing. The solution is built by integrating the leading cyber resilience capabilities of Commvault® Cloud with the highly secure, high-performance Pure Storage platform. Learn more about the solution and our commitment to cyber resilience in this solution brief.
Are You Cyber Ready?
Readiness reflects mature cyber resilience, where technology, people, and processes work seamlessly to enable business continuity in the face of any cyber challenge. Evaluate your organization’s cyber resilience with Commvault’s Cyber Maturity Assessment.
¹Key findings from the 2024 ESAs Dry Run exercise
²Countdown to DORA – Four Takeaway Points from Regulators’ December Statements