It has always been our intent to encrypt everything: all written data, all management data, the APIs, and HTTP, and only allow SSH for shell access, and then, of course, root access is impossible. We did this back in 2012 with our first array and it’s been the foundation of our secure-by-default focus ever since.
But still, we had one last concern: What if you had to physically lock the array down? It sounds wild, but the first customer who requested a method of physically locking array data was an organization that “forward deployed” FlashArray™ systems onto a battlefield. Since FlashArray only sips energy and needs just a few RUs to install, it’s a viable option for many military departments. But not “forward deployed.” Why? Because in the event that a location was overrun, it would be possible to transport the entire array and time can be critically short.
To address this, we integrated a specially programmed and customized FIPS-validated YubiKey, a small hardware security key that plugs into a USB port of your FlashArray. Need to transport an array? Need to lock down an array immediately? Just pull out the YubiKey and decryption is blocked.
That’s it. That’s Rapid Data Locking (RDL).

How Rapid Data Locking Works
Today, we’re excited to announce a new partnership with Yubico, integrating custom programmed YubiKey 5 FIPS devices as a hardware security key for our RDL. These little USB-based hardware keys contain a write-only passphrase that you make and load onto the device. After you write your passphrase to it, put the YubiKey into the FlashArray’s USB port and run the command to enable Rapid Data Locking. That’s it. Done.
Besides battlefield deployed arrays, there are also other security policies that simply require an external key to satisfy a specific requirement. In this scenario, as compliance or policy dictates, the keys can be kept separate from the array. The array still functions without the keys installed. The keys will need to be reinstalled for upgrades or to perform any recovery after a power failure.
For the record, you can also enable RDL with KMIP, which provides a remote key to a remote server over an encrypted connection. You can read more about that in this FAQ and best practices article (Pure1® registration required).

BUYER’S GUIDE, 12 PAGES
Your Complete Cyber
Resilience Buyer’s Guide
How FlashArray Encryption with RDL Works
Before we get into all the details about how RDL encryption works, you should know that adding RDL is non-disruptive. You won’t need to rewrite any data.
To oversimplify, every FlashArray contains a kind of puzzle, which, when assembled, provides data access. We start with the array encryption key that is created during initial deployment. This is the key that never changes. To protect it, it is partitioned, or split up, and then each separate “chunk” is hashed to each flash module’s device ID. This is a new key (an access key), and to gain access, you’ll need 50% of all flash modules, plus two, to access the array encryption key. When it all comes together, like a puzzle, you get the entire picture, or rather, all of the data.
The YubiKey is added to this process as a dependent factor, becoming critical to form the access key to the modules, which contain the array encryption key. Without the YubiKey, the modules cannot unlock, as represented below:
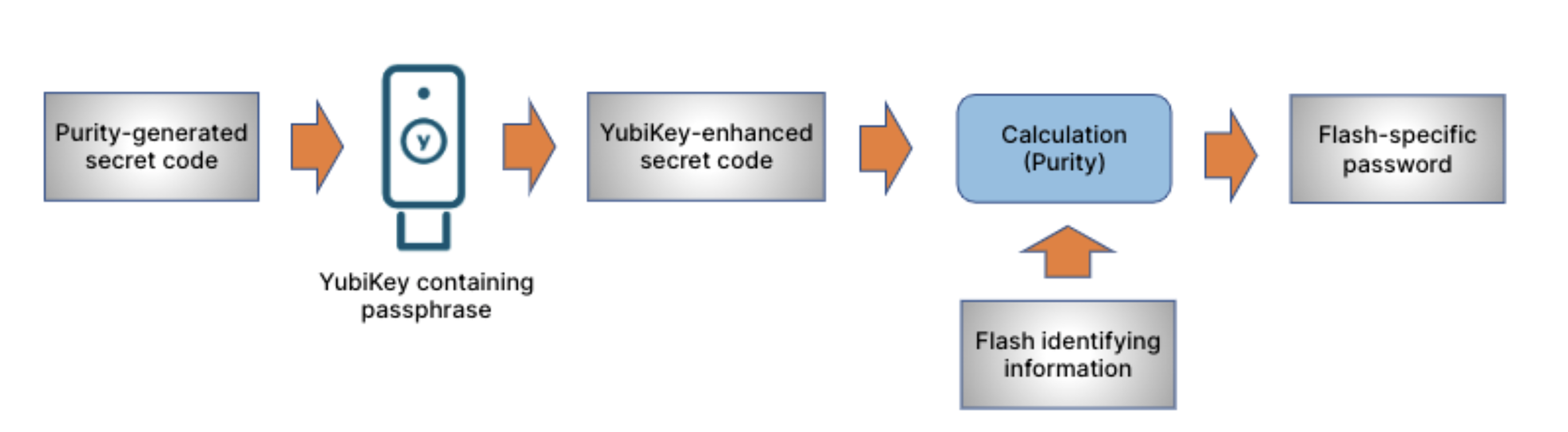 FlashArray RDL Leverages Multiple Factors: Secret Codes, Flash IDs, and Physical Keys
FlashArray RDL Leverages Multiple Factors: Secret Codes, Flash IDs, and Physical Keys
Here are the important facts you need to know:
- We have layers of access, and all layers must be present to decrypt array data. Bad actors can’t find a few flash drives and access the data. They would need more than half of the drives.
- The array encryption key uses AES-256 bit encryption and never changes.
- Rapid Data Locking inserts a write-only passphrase into the flash modules’ access key. This is why the YubiKey must be present at power on to unlock the modules. Because of how the key is applied, there’s no need to rewrite data after RDL enablement.
The YubiKey Advantage for RDL
We partnered with Yubico using their YubiKey 5 FIPS NFC keys, which have been custom programmed (and etched with our logo!. We wanted something as secure as FlashArray. Available exclusively through Pure Storage, these YubiKeys are FIPS validated, and have Near Field Communications (NFC) capabilities disabled to meet stringent compliance requirements. They offer an elegantly simple method of providing an external, physically revocable key with the following characteristics:
- Superior authentication: FIPS 140-2 validated to meet the highest authenticator assurance level 3 (AAL3) of NIST SP800-63B guidance.
- Easy, fast, and reliable: A modern, easy-to-use hardware authenticator, offering one-touch strong authentication. The devices are crush and water resistant, and do not require a battery or network connectivity to work.
They’re also simple to program with a passphrase, and one YubiKey is then inserted into the back of each controller. Replacement is easy if required, but loss of the passphrase will mean a fully locked array. We recommend setting up multiple YubiKeys for each FlashArray for that reason.
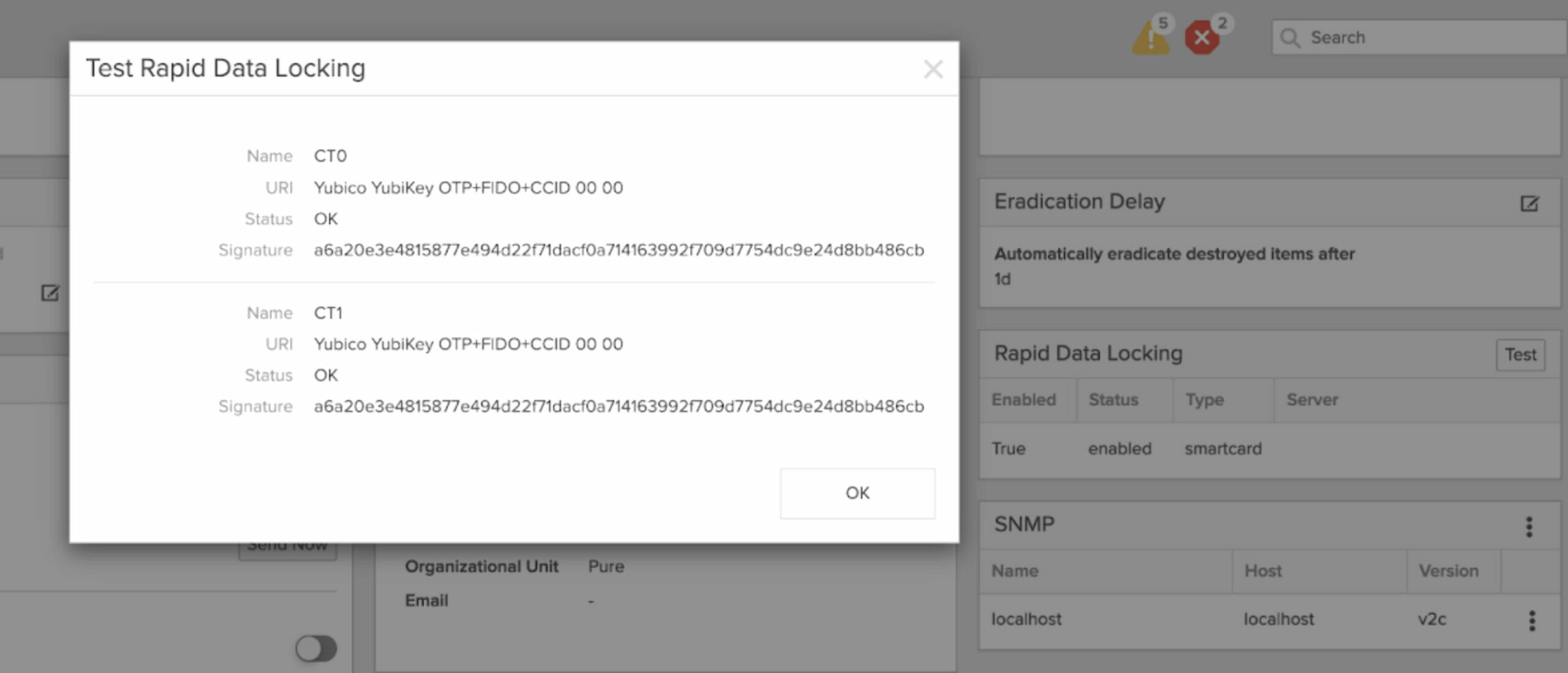
Be sure to run the RDL test in the FlashArray GUI to ensure your YubiKey is enabled for RDL.
Physical Data Security Built for Everyone, Everywhere
At Pure, we’re obsessed with ensuring your data’s security. Our partnership with Yubico is just one more piece of our already impressive pie. For sure, it was a challenge to improve upon our default security where everything is encrypted, from management traffic to every bit of written data, all wrapped up in such a way that to gain access to that data, attackers would need the entire array. And that led us to the next step—lock down the entire array with RDL.
Add to this the new options in physical encryption security, and you now have a complete solution to cover you if you need to transport an array, install it in a “forward deployed” location, or if your organization simply requires an external key for data access. Get our RDL package, set up your customized YubiKey 5 FIPS keys, and then enable RDL.
To get this and more in Purity//FA 6.4.3, upgrade your FlashArray fleet on your schedule through the self-service upgrade in Pure1.
Self-service Upgrades
Learn how you can upgrade your own FlashArray.