Summary
Tiered backup architectures—or, resiliency architectures—use different logical and geographic locations to meet diverse backup and recovery needs. When backups alone aren’t fast enough, data bunkers offer elegant solutions for resilience and eliminating data grvity. Here is just one example of an architecture you could implement with Pure Storage® technology.
This is part two of a series about air gaps and data resiliency architectures. See “What Are Air Gaps and Are They Effective Security Strategies?” for part one.
Say the worst-case scenario does happen—does your organization have what it takes to recover, and do it quickly?
If you’re using an air-gapped security strategy, you’re making it more challenging for malicious hackers inside or outside your organization to access sensitive data. It’s a preventive measure that helps increase your resiliency. However, you’re not doing much to improve your ability to get back to business after an attack. That’s because an air-gapped solution alone cannot address two elements crucial for resiliency:
- Accessibility. Post-attack, air-gapped vaults aren’t always easily accessible.
- Speed. Great protection is only half of the backup and restore story. Without underlying infrastructure that delivers accessibility and speed, your business is stuck waiting.
What type of solution can address simplicity, reliability, and speed before, during, and after an unexpected event? A tiered resiliency architecture with a data bunker option.
Beyond Prevention: A Next-gen Architecture That Enables Fast Recovery
Resiliency architectures use different logical and geographic locations to meet the diverse backup and recovery needs of many organizations, including those in the public sector and operating critical infrastructure.
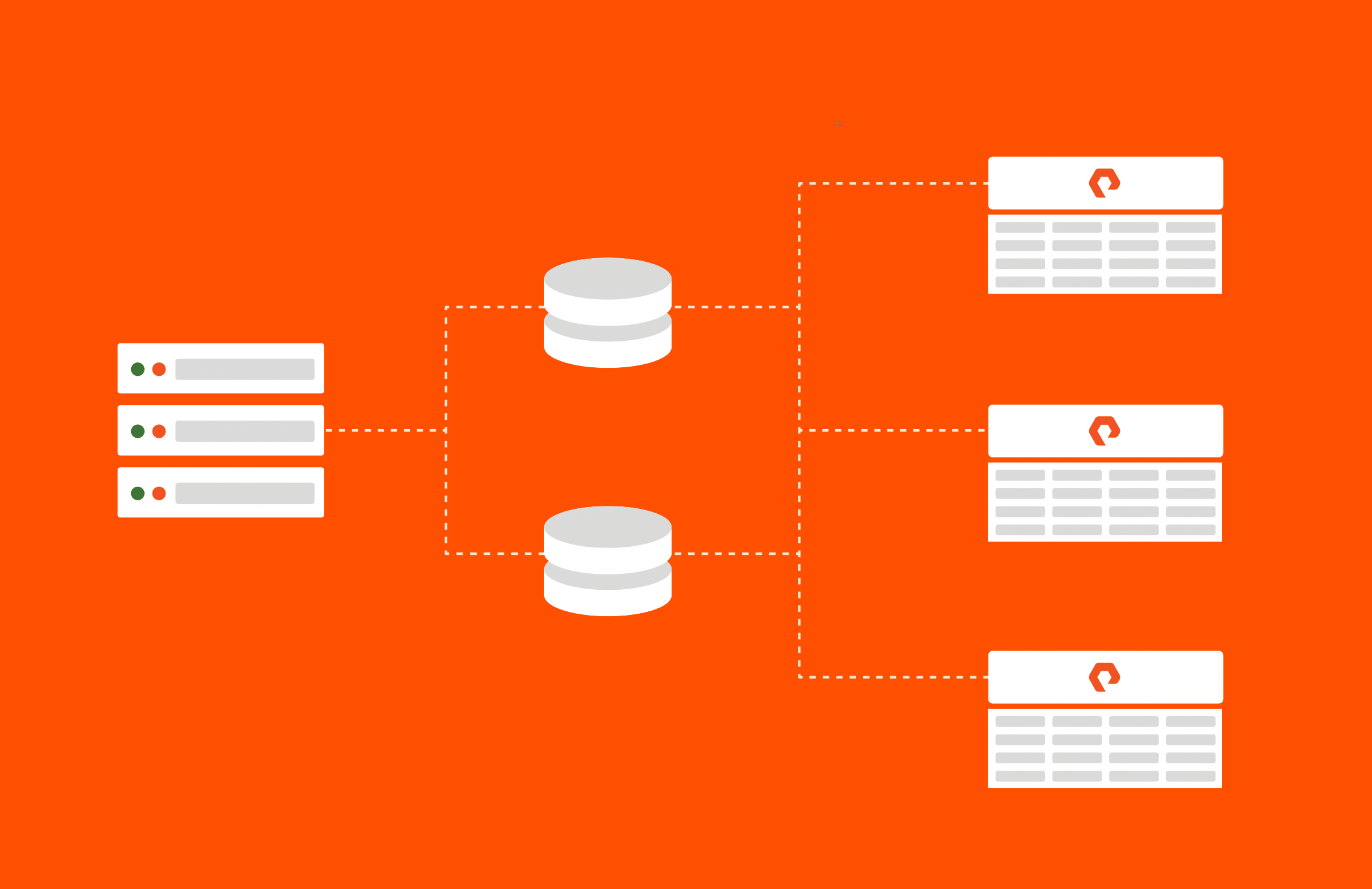
Below is just one example of a tiered resiliency architecture you could implement using the Pure Storage platform. (Note: You can easily adapt this approach to meet your specific goals and budget.)rage® technology. Note that this can easily be adapted to meet your specific goals and budget.
Figure 1: Example of a tiered resiliency architecture with a data bunker and Pure Storage® SafeModeTM protections (immutability plus more) against insider threats and advanced malware applied to all tiers. Some competitive solutions only apply immutability to the last tier.
Let’s take a closer look at this next-gen approach, breaking it down tier by tier.
Tier 0
Mission-critical infrastructure at this layer includes but is not necessarily limited to Active Directory (AD), DNS, and time services. Without these services, little or nothing else in the environment will function.
Tier 1: Active Failover
This is where you can host your primary data and critical business applications, including core databases and application services, along with their dependencies. These elements are the cornerstone of your business operations and the primary focus of recovery efforts, as their unavailability directly impacts your organization’s ability to deliver services to customers.
To minimize downtime, Tier 1 provides immediate or nearly immediate failover capabilities without requiring restoration from snapshots or backups. Solutions such as ActiveCluster™ from Pure Storage enable seamless failover between two systems located in close proximity (11ms or less latency between sites) with no data or performance loss. This ensures operational continuity even if one side of the cluster fails.
For customers that require failover across greater geographical distances or are outside the boundaries for synchronous replication, ActiveDR™ offers a low recovery point objective (RPO) and recovery time objective (RTO) failover solution, making it ideal for broader disaster recovery needs.
Tier 1 should retain three to seven days of SafeMode Snapshots to safeguard against data loss. Depending on your app’s performance requirements, you can employ FlashArray//X™, FlashArray//XL™, or FlashArray//C™ to create a high-performance, resilient foundation for this critical layer.
Tier 2: Local Snapshots
Tier 2 serves as a snapshot replica archive for storing offloaded snapshots from Tier 1, which also lives at this layer. Snapshots of Tier 1 data are taken on a regular, recurring basis—ranging from every 15 minutes to a few times a day. The snapshots are kept locally for a relatively short period (three to seven days) to provide near-instant recoverability if needed. However, the archive should be able to store the snapshots for longer—at minimum, three months (90 days) to 6-12 months or longer, if possible.
Tier 2 provides the fastest path to restoration with immediate rollback, ensuring minimal disruption to your operations. It’s also useful for longer-term forensics after an attack. And while Tier 2 is meant for storing data for the long term or meeting data compliance needs, you could, in the event of a major disruption, use this layer to run workloads at slightly lower performance to keep your business running.
You can build a snapshot archive on FlashArray//C, FlashBlade//S™, or FlashBlade//E™.
Tier 3: Primary Data Protection Site (aka The Disaster Recovery Site)
This layer can be a fast backup tier for extreme scenarios only—like a fire or tornado wiping out your primary data center. Generally, you should use the backup tier as a long-term retention layer for compliance or to restore data for applications that don’t warrant snapshot protection.
Here again, you could use FlashArray//C or FlashBlade//S with ISVs and enterprise application native solutions integrated to allow backup data to be written directly to the array and protected with immutable snapshots and Pure Storage SafeMode. (SafeMode snapshots provide additional protection from ransomware or the deletion or corruption of your backup data.) You could also use FlashBlade//E to replace traditional spinning disk backups.
Tier 4: An Optional, Data-only Bunker
If you’re using Pure Storage to build a tiered resiliency architecture, you have the option to create a Tier 4 layer of defense on FlashArray//C or FlashBlade//S. You can also build this layer by using public cloud S3 targets or cloud-adjacent bare metal services such as Equinix Metal. But generally, you’d want higher-speed storage like FlashArray//X or FlashBlade//S for Tier 4, as the intent is to run just as current production would, only in a different location.
Now, let’s dig into why your organization would want to build a data bunker.
Data Bunkers: The Secret Weapon for Recovery and Resiliency
Traditionally, Tier 4 would have used tape storage, but that approach has little purpose today, even for long-term data retention. With a Tier 4 data bunker, you get a one-way-in data lake to retain large amounts of data available for immediate use.
Data bunkers are highly secure and provide an extra layer of durability as optional disaster recovery sites serving behind your primary and secondary backup sites. Host a replicated copy of data and make compute available on demand. Potentially, you could store years of data at the Tier 4 layer.
Bunkers can be especially useful when an entire geographic region is impacted by an adverse event and/or it is impractical to restore data. But they also offer an elegant solution to the conundrum of data gravity. Imagine a general moving all critical military operations underground after an air raid. Similarly, in the event of a disaster, you could establish compute resources in a bunker and move your mission-critical applications to the data until a primary and/or secondary data center is rebuilt or recovered.
Sure, data-only bunkers at Tier 4 can be considered “optional.” But in today’s threat environment, and in a world where major disasters happen all too frequently, why wouldn’t you want this additional layer of defense that can shore up your resiliency—and ensure an even faster recovery?
Getting Started: How to Enable Your Pure Storage Tiered Resiliency Architecture
Once you’ve decided how many layers of defense you need, and which Pure Storage flash storage arrays you want to use to build and support your resiliency architecture, you’ll need to do the following:
- Store the data for the workloads you want to protect on your Pure Storage array.
- Enable snapshots on those arrays and set up protection groups to support your desired disaster recovery objectives.
- Let the snapshots run for a couple of weeks, based on your defined policies. This process will help ensure protection group policies are proven to be configured accurately. It will also allow you to tune the policies without having to invoke the out-of-band process with Pure Support.
- Enable Pure Storage SafeMode to protect snapshots from accidental or purposeful deletion and eradication. (Remember that after you turn on SafeMode, the only way to change protection group settings or disable SafeMode is through a special Pure Support process.)
Step Into the Future of Resiliency with Pure Storage
While you don’t have to use Pure Storage technology to build a tiered resiliency architecture with data bunkers, here’s why you should: Without our platform at the foundation of your architecture, and without capabilities like SafeMode, you can’t create a truly next-gen solution for backup and recovery.
A Pure Storage Tiered Resiliency Architecture is the future of disaster recovery. It brings advanced resilience, performance, and simplicity to help your organization truly revolutionize its legacy, antiquated backup environment. And with SafeMode protection built into every tier with immutable snapshots for additional resiliency, you’re even safer from malware attacks and accidental or rogue deletions.
Have more questions about the benefits of a Pure Storage Tiered Resiliency Architecture? Contact us.
Ransomware is getting smarter every day, but with Pure backup and recovery solutions, we can outsmart threats together.

White Paper, 7 pages
Learn What’s Helping CISOs Sleep Better at Night
And how you can too.

Stay Resilient
Fortify your data and guarantee uninterrupted business operations.