Summary
Tiered backup architectures—or, resiliency architectures—use different logical and geographic locations to meet diverse backup and recovery needs. When backups alone aren’t fast enough, data bunkers offer elegant solutions for resilience and eliminating data grvity. Here is just one example of an architecture you could implement with Pure Storage® technology.
This is part two in a series about air gaps and data security architectures. Check out What Are Air Gaps and Are They Effective Security Strategies? for part one.
In my previous post, I explained the concept of “air gaps” and how some data storage vendors use them to help prevent an attack. But what happens when disaster does strike?
When Colonial Pipeline was hit with a ransomware attack, they ended up using their own backups to restore the system. But the backups were too slow. The process took days and the delays had devastating effects.
Had they utilized data bunkers, in combination with tiered backup architectures, the story would have been different.

Prevention is Only Half of the Battle
Data protection strategies can’t just cover the before of an event—they have to meet expectations after an event, too. Air gaps may help add an extra layer of prevention, but after an event, two things are critical that an air-gapped solution alone cannot address:
- Accessibility. Post-attack, air-gapped vaults aren’t always easily accessible.
- Speed. Great protection is only half of the backup and restore story. Without underlying infrastructure that delivers accessibility and speed, your business is stuck waiting.
What, then, can help you address simplicity, reliability, and speed—before, during, and after an unexpected event?
Create Resiliency with a Tiered Backup Architecture and Data Bunkers
Tiered backup architectures—or, resiliency architectures—use different logical and geographic locations to meet diverse backup and recovery needs.
Below is just one example of an architecture you could implement with Pure Storage® technology. Note that this can easily be adapted to meet your specific goals and budget.
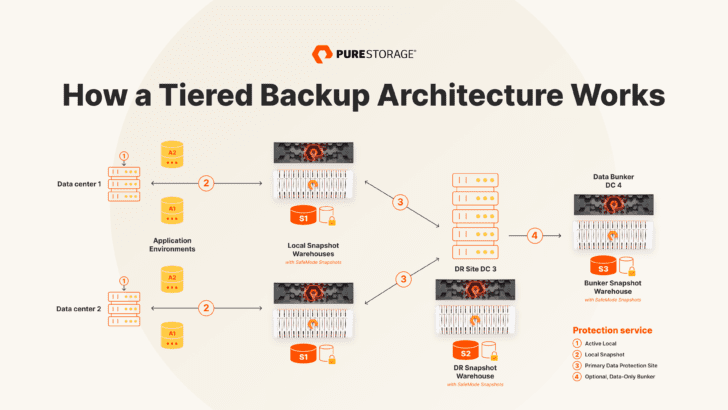
[Example of a tiered architecture with a data bunker, and Pure SafeMode™ protections (immutability plus more) against insider threats and advanced malware applied to all tiers. Some competitive solutions only apply immutability to the last tier.]
Let’s take a closer look at each tier.
Tier 1: Active Failover
Generally, this tier provides an immediate or nearly immediate failover without the need to restore from snapshots or backups. Technology, such as Pure ActiveCluster™, provides immediate failover between two systems located in close proximity (11ms or less latency between sites) with no data or performance loss should either side of the cluster fail.
For customers outside of the geographical boundaries required to perform synchronous replication, or for those who choose to replicate across longer distances, Pure ActiveDR™ can be leveraged to provide a very low RPO and RTO failover solution.
Tier 2: Local Snapshots
Snapshots of Tier-1 data are taken on a regular, recurring basis—from every 15 minutes to a few times a day. These are kept locally for a relatively short period of time (three to seven days) to provide near-instant recoverability should the need to restore occur.
This tier is useful to quickly restore from with immediate rollback after administrative mistakes or bugs in development.
Tier 2a: Local Snapshot Protection
Additionally, local snapshot protection can extend the recoverability available for a quick restore from short-term data loss. Generally, this tier will offload local snapshots from the primary array and store them on a secondary array for a slightly longer period of time (e.g., 14 to 30 days). This frees up storage on the primary array but still provides extremely high-speed restores when necessary. The snapshots all provide immutable and enhanced protections to prevent them from being deleted from the local array.
Tier 2b: Data Protection Software
Data protection partners and backup vendors can be integrated into this tier, offering a very fast restore of recent backup data in the event of a cyberattack. On Pure systems (either FlashArray™ or FlashBlade®), backup vendors can offer advanced recovery options through custom integrations and architectures built with Pure.
Tier 3: Primary Data Protection Site (a.k.a., DR Site)
From Tier 2, 30 to 360 days of backup snapshots could be replicated to a Tier 3 site for medium-term recoverability from a disaster that might strike an entire, primary data center location such as a fire or tornado. This tier is meant to be a secondary disaster recovery (DR) site that is physically and geographically separate from the primary site, with advanced backup integrations for fast recoverability. SafeMode snapshots provide additional protection from ransomware or the deletion or corruption of backup data.
Tier 4: An Optional, Data-Only Bunker
Traditionally, Tier 4 may have used tape storage. But today, tape serves little purpose, even for long-term data retention. That’s where a Tier 4 data bunker comes into play, serving as an additional, one-way-in data lake for retention of large amounts of data available for immediate use. Bunkers can be especially useful when an entire geographic region is impacted and/or it is impractical to restore data—but that’s not all they can do.
Data Bunkers: The Secret Weapon for Recovery and Resiliency
Just like underground bunkers were critical military defenses, data bunkers are excellent defenses against today’s threats. As an optional, additional DR site behind primary and secondary backup and DR sites, a data bunker offers a highly secure, extra layer of durability.
Bunkers also offer an elegant solution to the conundrum of data gravity. Imagine a general moving all critical military operations underground after an air raid. You could establish compute resources in a bunker and move your mission-critical applications to the data until a primary and/or secondary data center is rebuilt or recovered.
To recap, a data bunker:
- Is incredibly fast and highly secure. Given that communication is established into, but not out of, the bunker, it’s considered a highly secure location.
- Keeps large amounts of data in a usable state. Bunker data is in a highly accessible form, on relatively slower media, and can be used as the ultimate recovery point should a major disaster strike.
- Makes storing large amounts of data affordable, via data reduction and/or QLC economics.
- Stores long-term data stretching back years. This data can serve other purposes, such as analytics, compliance, or regulatory needs.
- Is data only and continuously replicated to. A bunker does not run production compute resources under normal circumstances.
- Is generally one-way-in, with no or limited egress. Data in the bunker could be used for limited purposes and wouldn’t be intended to exit the bunker under normal circumstances.
Recover Faster with Pure
Implementing a resiliency architecture is an excellent way to build resilience and durability into your recovery strategy, but doing so with Pure Storage takes it a step further. With SafeMode protection built into every tier with immutable snapshots for additional resiliency, you’re even safer from malware attacks and accidental or rogue deletions.
Ransomware is getting smarter every day, but with Pure backup and recovery solutions, we can outsmart threats together.





