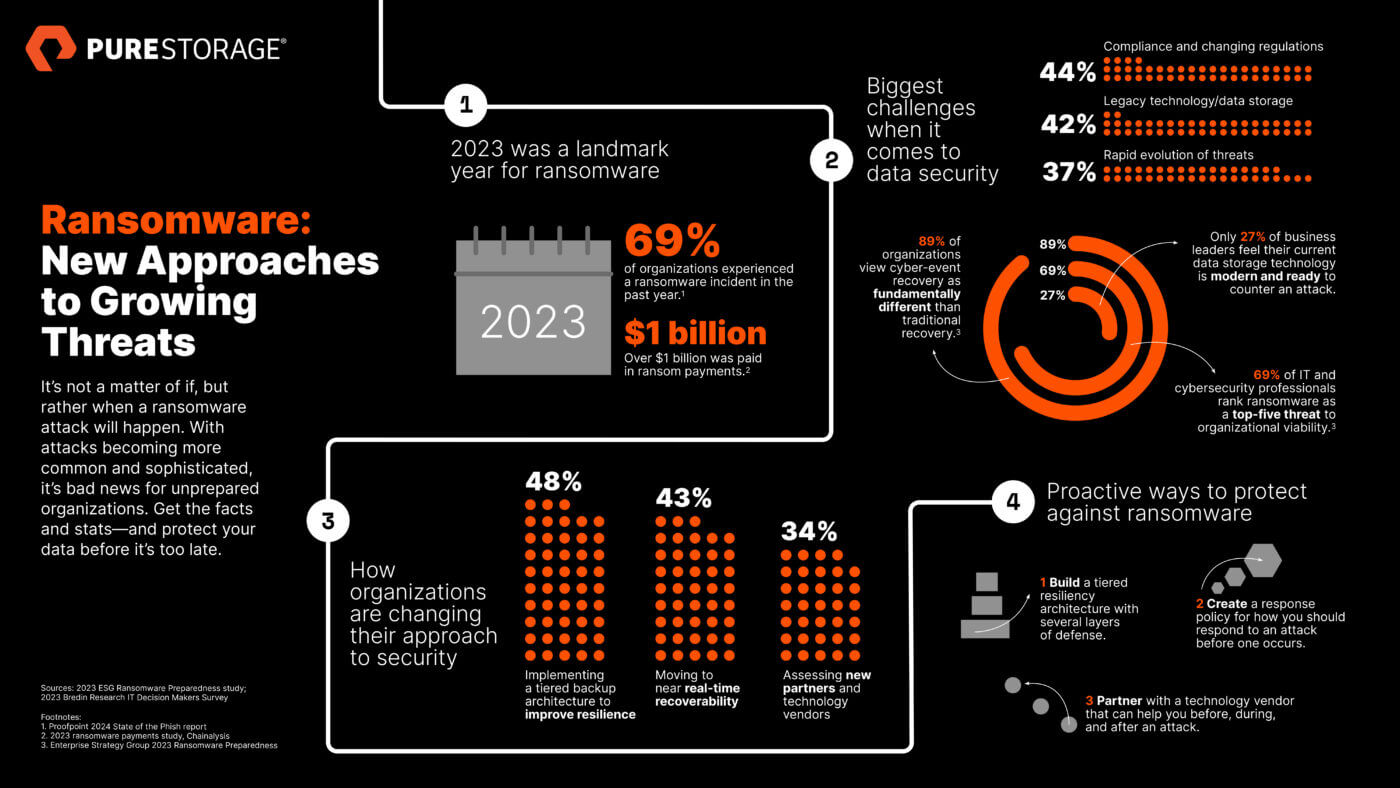
In the treacherous world of cybercrime, ransomware attacks have been making headlines for quite some time. These malicious software threats encrypt a victim’s data, demanding a ransom for its release. While ransomware attacks are nothing new, a particularly sinister variant known as “scareware” ransomware has been causing chaos in recent years. This blog delves into the world of scareware ransomware attacks to examine the motives behind these attacks and the strategies you can deploy to safeguard against them.

BUYER’S GUIDE, 12 PAGES
Your Complete Cyber
Resilience Buyer’s Guide
The Anatomy of Scareware Ransomware Attacks
Scareware ransomware attacks, also known as “fake” or “rogue” ransomware, are a cunning evolution of traditional ransomware. Unlike their counterparts, scareware attacks may not encrypt your files at all. Instead, they rely on psychological manipulation to trick victims into paying a ransom. Here’s how they typically unfold:
- Infection: Scareware can sneak into your system through phishing emails, malicious downloads, or compromised websites. Once in, it may not immediately reveal itself, lurking silently in the background. This “dwell time” can last for hours, days, or even weeks.
- Fake alarms: At the chosen time, scareware springs into action, bombarding the victim with pop-up messages or notifications. These messages claim that the user’s computer is infected with a devastating virus or malware.
- Threats and intimidation: To intensify the fear, scareware messages may threaten to delete files, expose sensitive data, or even claim to involve law enforcement agencies in the investigation.
- Ransom demand: The victim is presented with a demand, often payable in cryptocurrency, in exchange for a supposed remedy or to prevent the dire consequences promised by the scareware.
- Payment pressure: Scareware creators employ aggressive tactics, such as countdown timers or escalating threats, to pressure victims into making a hasty payment.
Download the report, “Lighting the Way to Readiness and Mitigation,” to learn strategies IT cybersecurity professionals are implementing to protect their organizations from these threats.
The Psychological Warfare of Scareware
Scareware attacks are like a horror film playing out on your computer screen. They exploit fear, urgency, and uncertainty to manipulate victims into paying the ransom. Here are some psychological tactics that scareware employs:
- Fear of loss: Scareware plays on the fear of losing valuable data or facing legal consequences.
- Urgency: The countdown timers and impending doom scenarios create a sense of urgency, making victims act impulsively.
Guarding against Scareware Ransomware Attacks
The best defense against scareware attacks is a combination of vigilance, cybersecurity measures, and knowledge:
- Stay informed: Be aware of the latest scams and threats circulating in the digital realm. Knowledge is your first line of defense.
- Maintain system hygiene: Ensure your operating system and software applications are up to date with the latest security patches.
- Back up your data: Regularly back up your important files to an external device or a secure cloud storage service. Pure Storage works with leading data protection companies, including Commvault, Veeam, Veritas, and Rubrik.
- Think before you click: Avoid clicking on suspicious links or downloading attachments from unknown sources, especially in unsolicited emails.
Scareware ransomware attacks are a testament to the ever-evolving nature of cybercrime. These malicious actors have honed their tactics to prey on our deepest fears and vulnerabilities. However, by staying informed, implementing strong cybersecurity practices, and keeping a cool head in the face of digital threats, you can fortify your defenses against these sinister digital nightmares. Remember, the best way to defeat scareware is to deny it the satisfaction of a ransom payment and to report the incident to the appropriate authorities. In the battle against cybercrime, knowledge and resilience are your greatest allies.
Written By:
Are You Prepared?
See best practices and strategies cybersecurity professionals are using to combat ransomware.