Summary
Released in Purity version 6.6.7, encrypted replication provides end-to-end encryption with TLS 1.3, enhances the security of replicated data, and is optimized for minimal impact.
Encrypted replication has been available since Purity version 6.6.7, where we introduced over-the-wire encryption with asynchronous replication (async and ActiveDR™). We’re planning to include encryption capabilities for ActiveCluster™ replication in upcoming releases, enhancing data security across various replication topologies.
The main features and benefits of encrypted replication are:
- End-to-end encryption with TLS 1.3: Data is replicated via asynchronous connections with protection group-based asynchronous replication and ActiveDR. Replication is now encrypted using TLS 1.3, ensuring secure data transmission.
- Pre-shared key (PSK) security: High-entropy PSKs, uniquely generated for each array pair, enhance the security of replicated data.
- Seamless migration: Customers currently using asynchronous replication can easily transition to encrypted replication with minimal impact to their existing workflows.
- Minimal performance impact: Our comprehensive performance analysis ensures that the encryption process is optimized for minimal impact on replication performance.
- Simplified user experience: The introduction of a new connection-key format and streamlined CLI commands significantly improves the user experience for setting up and managing encrypted array connections.
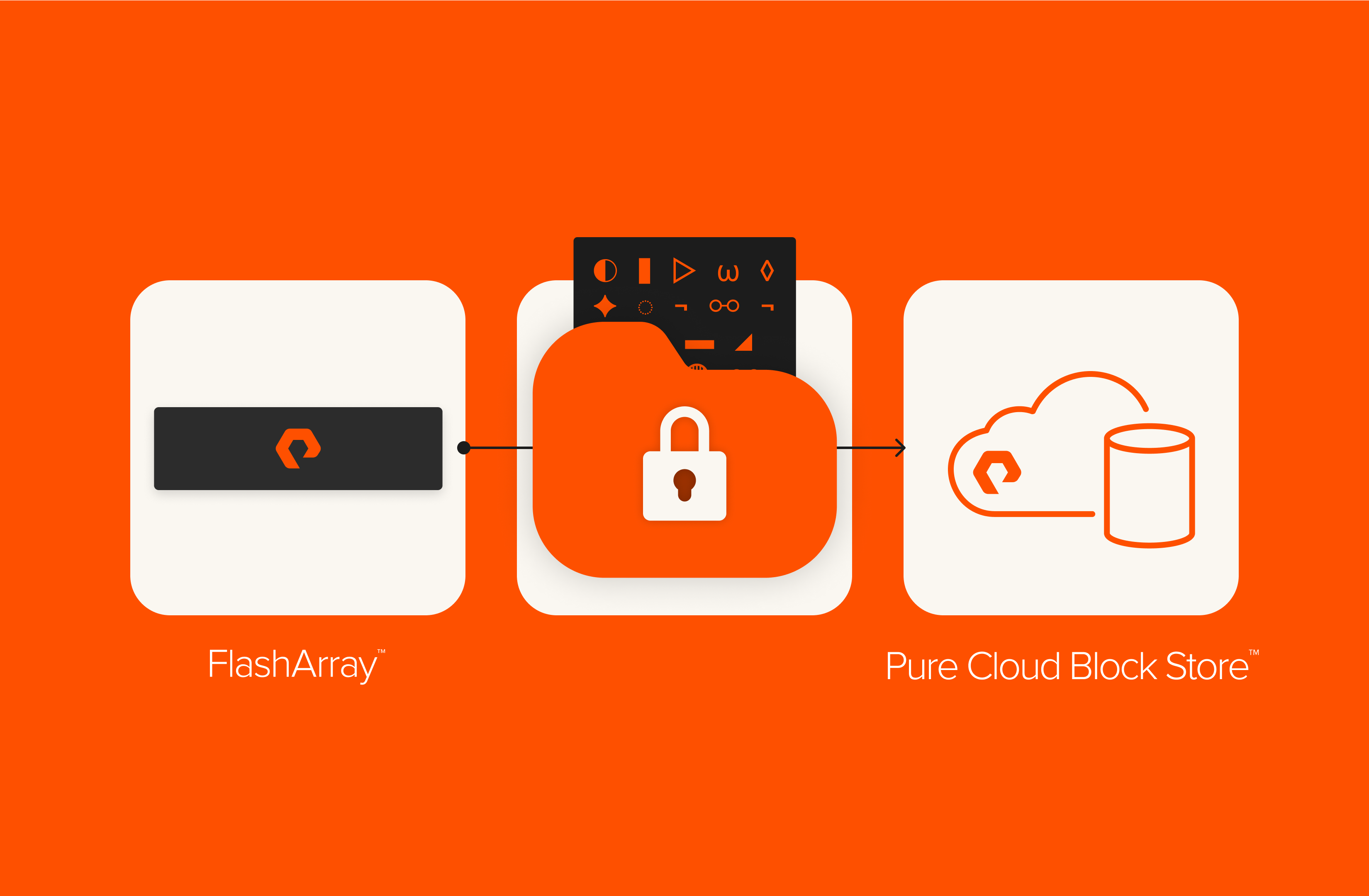
Encrypted replication can be established between FlashArray™ systems, between Pure Cloud Block Store™ arrays, and in a hybrid environment between FlashArray and Pure Cloud Block Store. In our test case, we’ll show encrypted asynchronous replication between an on-premises FlashArray and the cloud array running Pure Cloud Block Store on Microsoft Azure.
The Purity//FA software uses the AES-256 algorithm in counter mode to encrypt all data and most metadata stored locally. For asynchronously replicated data in flight, encryption end to end (array to array) is achieved with TLS 1.3 using a pre-shared key (PSK). This safeguards data from advanced persistent threats and man-in-the-middle (MiTM) threats. Encryption with PSK requires key generation; we provide options to securely store and manage these keys, including periodic rotation similar to certificate management.
Figure 1: Encrypted replication over the wire.
Encrypted Replication Setup
Setup of encrypted replication is easy and can be done in three simple steps.
First, log in to the web user interface of the designated target FlashArray or Pure Cloud Block Store. Navigate to Protection > Array and create an encrypted connection key for the array. Copy the generated key for use in the connection setup.
Figure 2: Generate encrypted connection key.
On the source FlashArray or Pure Cloud Block Store, navigate to Protection > Array and connect the target array with a copied encrypted connection key.
Figure 3: Configure connection between arrays.
And that’s all. Now we can see our configured connection in the array connection list.
Figure 4: Array connections overview.
The same steps can be used to configure the connection via Purity CLI using the purearray connect –encrypted command on the local array.
Step 1: List and copy the encrypted pre-shared key (PSK) on the remote array:
purearray list –connection-key –encrypted
Step 2: On the local array, connect to the remote array using the encryption keys (enter the connection key when prompted):
purearray connect –encrypted –management-address <target-management-address> –replication-address <target-replication-address> –replication-transport ip –type async-replication
Step 3: Verify the encrypted replication connection status:
purearray connection list
Our benchmarks indicate that enabling encryption on asynchronous replication has minimal impact on performance, with about a 5% utilization of total available IOPS, and in some cases of recovery point objective (RPO), increasing by 10% (500ms – 1min).
For a demo, watch the video:
Learn More
See the simple steps for setting up encrypted replication.