Summary
Learn how to securely store and retrieve passwords for the Pure Storage PowerShell SDK, now updated with AES encryption, improved portability, and the latest FlashArray PowerShell SDK 2.16 for enhanced security and flexibility.
Quick post on how to store and retrieve passwords to automate login to the Pure Storage FlashArray using the PowerShell SDK.
We will use the basis of a previous post, Using the PSCredential Object with the Pure Storage PowerShell Toolkit, and extend support for retrieving from a secure file.
The following line of PowerShell has to be run one time to create and store a secure password that maps to the default pureuser account. Make sure that the password you are creating is indeed the password assigned to the pureuser account on the FlashArray. This will use the Read-Host cmdlet to display a dialog to enter a password in the form of a secure string. The file in this example is stored in the C:Temp folder in a file named Secure-Credentials.txt
|
1 |
Read–Host –AsSecureString | ConvertFrom–SecureString | Out–File ‘C:TempSecure-Credentials.txt’ |
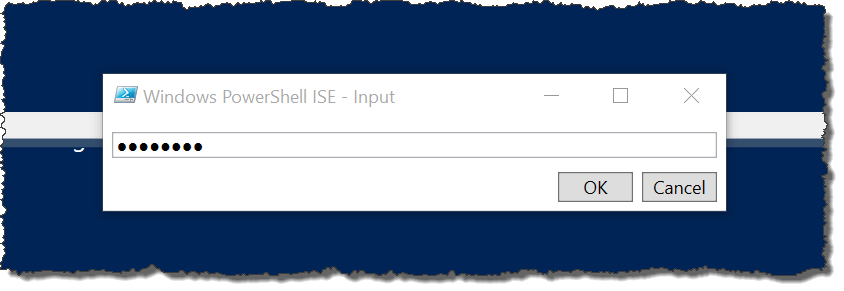
If you open the Secure-Credentials.txt file you would see the following:
Now the password has been stored securely. The only time that the Read-Host cmdlet would be required again is to update the secure password in the file.
Using the basis from the previous post noted above we use the same script except changing the $Pwd variable to be retrieved from the Secure-Credentials.txt file.
|
1 2 3 |
$Pwd = Get–Content ‘C:TempSecure–Credentials.txt’ | ConvertTo–SecureString $Creds = New–Object System.Management.Automation.PSCredential (“pureuser”, $pwd) $FlashArray = New–PfaArray –EndPoint 10.21.8.17 –Credentials $Creds –IgnoreCertificateError |
Now you can automate any script using the Windows Task Scheduler or other orchestrations tools.
Updated Approach:
To align with current best practices and leverage the latest SDK features, consider the following updated method for securely storing and retrieving passwords:
1. Utilize the Latest PowerShell SDK:
- Installation: Ensure you have the latest version of the Pure Storage PowerShell SDK installed:powershellCopyEdit
Install-Module -Name PureStorage.FlashArray -Force -AllowClobber
2. Secure Password Storage Using AES Encryption:
- Generate an Encryption Key: Instead of relying on DPAPI, generate a secure AES key that can be used across different systems:powershellCopyEdit
$Key = New-Object Byte[] 32 [Security.Cryptography.RNGCryptoServiceProvider]::Create().GetBytes($Key) [System.IO.File]::WriteAllBytes("C:\Temp\AESKey.key", $Key) - Encrypt and Store the Password: Use the generated AES key to encrypt the password:powershellCopyEdit
$Password = Read-Host -AsSecureString $Key = [System.IO.File]::ReadAllBytes("C:\Temp\AESKey.key") $EncryptedPassword = $Password | ConvertFrom-SecureString -Key $Key $EncryptedPassword | Out-File "C:\Temp\SecurePassword.txt"
3. Retrieve and Decrypt the Password:
- Load the AES Key and Decrypt: When accessing the password in your scripts:powershellCopyEdit
$Key = [System.IO.File]::ReadAllBytes("C:\Temp\AESKey.key") $EncryptedPassword = Get-Content "C:\Temp\SecurePassword.txt" $SecurePassword = $EncryptedPassword | ConvertTo-SecureString -Key $Key $Credentials = New-Object System.Management.Automation.PSCredential("pureuser", $SecurePassword)
4. Establish Connection Using Updated SDK Cmdlets:
- Connect to FlashArray: Utilize the updated cmdlets for establishing a connection:powershellCopyEdit
$FlashArray = Connect-PfaArray -EndPoint "10.21.8.17" -Credentials $Credentials -IgnoreCertificateError
Benefits of the Updated Approach:
- Enhanced Security: By using a consistent AES encryption key, the password can be securely decrypted across different systems and user contexts.
- Portability: Scripts and encrypted passwords can be transferred between systems without encountering decryption issues inherent to DPAPI.
- Alignment with SDK Enhancements: Leveraging the latest SDK ensures compatibility with new features and improvements.
Conclusion:
While the original method for storing and retrieving passwords in the PowerShell SDK was effective at the time, adopting the updated approach with AES encryption and the latest SDK version provides improved security, flexibility, and alignment with current best practices.