As I have blogged about before, TLS 1.0 and SSL v3 were deprecated in Purity 4.7, requiring all connections to use either TLS 1.1 or TLS 1.2. This affected a variety of integrations, some we updated, some you just had to alter their behavior. A few VMware products do not/did not use TLS 1.1/1.2 by default, so they either need to altered or upgraded. This almost invariably boiled down to the JDK version that was in use. vRealize Orchestrator is no exception.
When it comes to earlier version of vRO, like 6.0.3 and earlier, the certificate import process seem to not use TLS 1.1 or 1.2, so importing the certificate fails for the FlashArray running Purity 4.7 and later. Without the cert loaded, you cannot make any calls to the FlashArray. By default, 6.04 and later will work out of the box, as I think indicated in this KB and release notes.
Anything running JDK 1.7 will fail as TLS 1.1 and 1.2 is not enabled for clients by default until 1.8.
If you SSH into your vRO server and run the following you can find the JDK version:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
if type –p java; then echo found java executable in PATH _java=java elif [[ –n “$JAVA_HOME” ]] && [[ –x “$JAVA_HOME/bin/java” ]]; then echo found java executable in JAVA_HOME _java=“$JAVA_HOME/bin/java” else echo “no java” fi if [[ “$_java” ]]; then version=$(“$_java” –version 2>&1 | awk –F ‘”‘ ‘/version/ {print $2}’) echo version “$version” fi |
The results in vRO 6.0.3:
|
1 |
version 1.7.0_85 |
In vRO 7:
|
1 |
version 1.8.0_72 |
So how you do get the vRO 6.0.3 and earlier to work? There are two options:
- Manually installing the certificate.
- Altering the vRO JDK to enable TLS 1.1 and 1.2 use.
Note that the rest of the FlashArray workflows besides the cert import will work without any changes. All of the other workflows leverage the REST plugin, which seems to leverage the proper TLS version by default. So these workarounds are only to get the certificate to import to vRO.
Manually installing the FlashArray cert in vRO
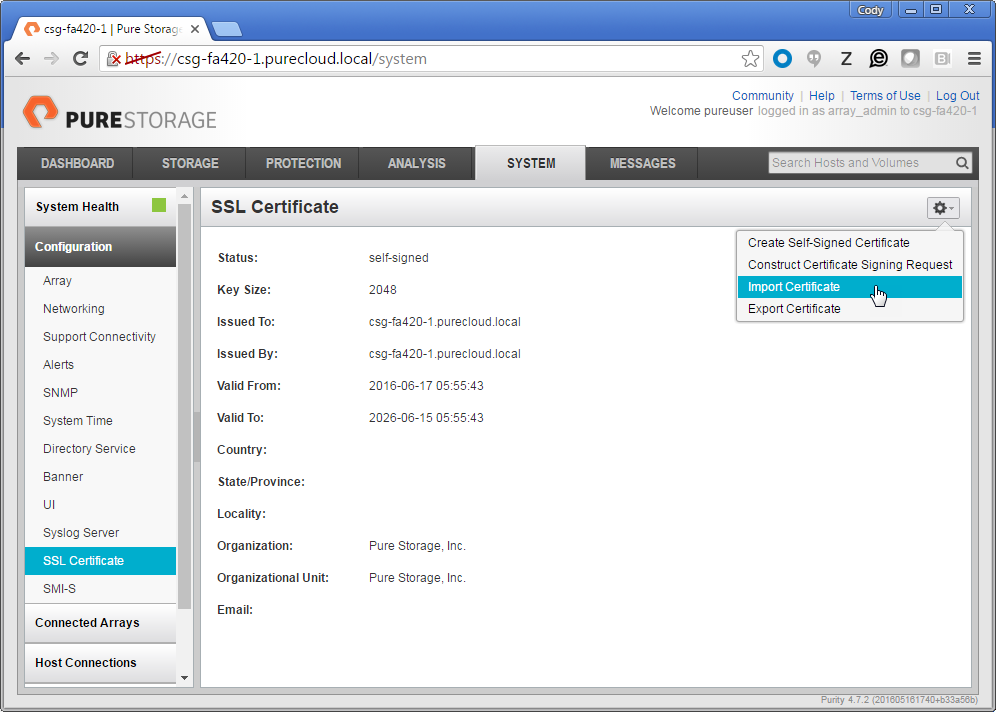
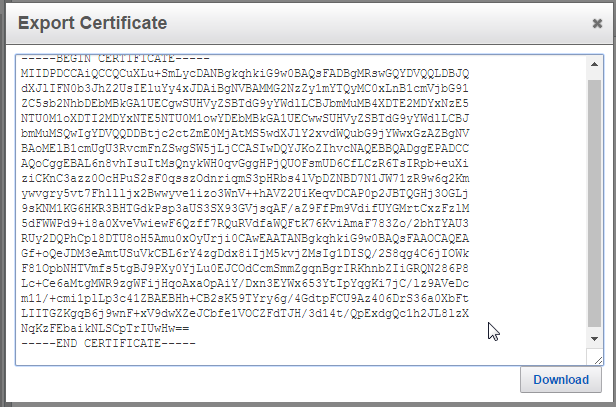
First go to your FlashArray GUI to the System tab and click on Configuration > SSL Certificate.
Download and save the cert to your local machine.
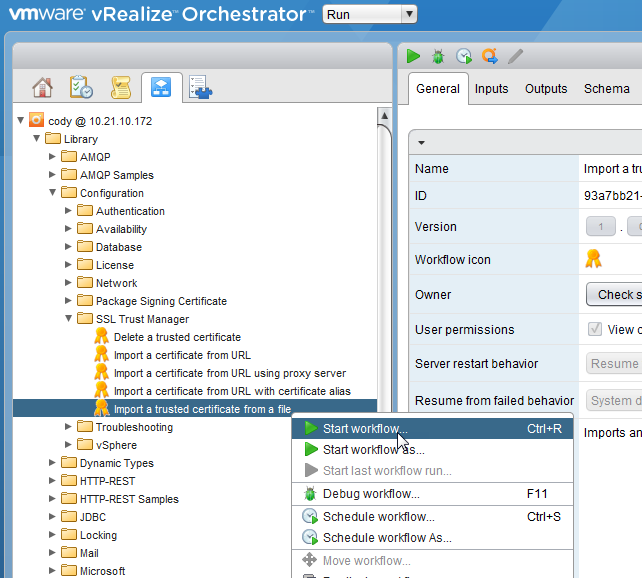
Then log into vRO and start the “Import a trusted certificate from a file” workflow.
 This will import your cert, bypassing the cert TLS issue.
This will import your cert, bypassing the cert TLS issue.
Enable Client-Side TLS 1.1/1.2 connectivity in vRO
The other option, is to allow JDK inside of vRO to use TLS 1.1 and 1.2. This is pretty simple, but any time you SSH into an appliance and make manual changes you need to be sure you know what you are doing. It is very unlikely to cause an issue, so you might want to confirm the change with VMware support. That being said, the VMware KB above does mention making a similar change, so I believe it is supported. Any, SSH into your vRO appliance as root and edit the following file:
/var/lib/vco/app-server/bin/setenv.sh
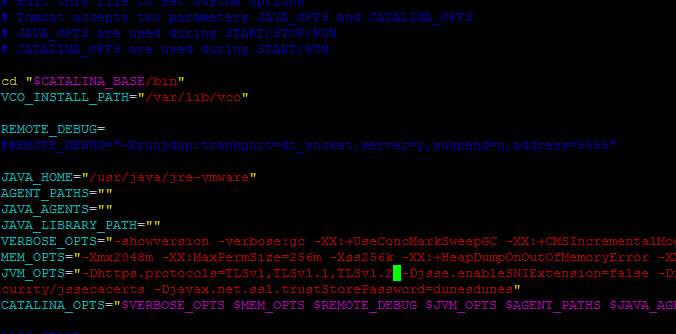
Using VI or whatever, edit the line starting with JVM_OPTS=”. Add in the start the following: -Dhttps.protocols=TLSv1,TLSv1.1,TLSv1.2 and then a space before the next value. Should look like below:
Save it and then reboot your appliance. The KB from VMware says restarting the vRO service works, but it did not work for me. I had to start the entire appliance. Once it came up, I was able to add certificates in the normal fashion.