This is part one in a series about air gaps and resiliency architectures. Read part two: Without A Tiered Backup Architecture, Are You Truly Resilient?
Ransomware attackers are ruthless opportunists—but that doesn’t mean we should make their jobs any easier.
Take the attack on Colonial Pipelines’ back offices. The critical gas and fuel infrastructure was offline for more than four days. An investigation revealed that big lapses in security made it “fairly easy” to break in.
We should be making life as hard as possible for hackers. Thankfully, there’s an arsenal of technologies and architecture paradigms to do just that. One of these approaches is called “air gaps”—but are they a silver bullet for cyber resilience?
What Is an Air Gap?
Is an air gap a must-have, marketing lingo, or both? Let’s take a look.
Traditionally, an air gap was physical, using tape-based backups or offsite systems, separated with zero physical connectivity. Administrators create a connection between the production system and air-gapped system, like a drawbridge. The bridge goes down when data is transferred, then goes back up the rest of the time.
Today, the definition and concept of “air gaps” is evolving past the traditional “physical network isolation” to be a valuable component of an effective, efficient data security strategy. Modern air gaps focus more on logical separation, primarily with network controls. Essentially, they are network design topologies that separate production and backup networks. Some vendors have adapted the concept into:
- “Virtual” air gaps. These were first introduced by vendors who wanted to focus on logical network separation and sell a duplicate set of infrastructure with Write Once, Read Many (WORM) capabilities. The network between sites would open and close periodically. This was delivered via extensive consulting and Professional Services.
- “Operational” air gap. When the “virtual air gap” had a tepid reception from customers (i.e., low sales), operation air gaps were created in a bid to reduce infrastructure costs and add additional automation around the setup and maintenance.
At their cores, both of those approaches most often rely on WORM capabilities built for regulatory and compliance requirements.*
The goal of an air gap is to isolate critical data from local networks and production areas that are more vulnerable to attacks. By allowing data in from the production network at regular intervals, backups are regularly updated, but the two sides are not always connected. These intervals could happen once a day or on any defined frequency.

Safeguard Your Data—and Your Business
Ensure effortless business continuity and data recovery.
The Air Gap Promise
The idea is that without an open connection between the two sites, threats theoretically have no bridge across. And without compute nodes, air-gapped systems are even less accessible. Some data storage providers tout these air-gapped recovery vaults as a modern innovation to keep data safe. A so-called air gap could even be something simple and programmatic, such as a firewall.
In general, air gaps can deliver enhanced protection by:
- Providing greater security than traditional backup architecture.
- Limiting the ability for malware to spread.
- Creating more work for hackers to get to air-gapped data.
- Improving the odds of recovering from an attack
And post-attack, air gaps can also be beneficial for recovering uncompromised data. But there’s more to consider.
The Reality of Air Gaps
There are a few issues to consider with air gaps. The first is accessibility. After an attack, when every second counts, an air-gapped vault hasn’t just made data difficult to access for hackers—it’s difficult for you to access, too. The second is the work involved to maintain air gaps. The more substantial an air gap gets with complex scripting, the more care and feeding it requires to stay operational and effective.
Other issues:
- They’re not 100% immune to attack.
- They can be expensive to implement and operate, and difficult to manage and maintain.
- They’re not super scalable and can be slower to recover large volumes of data.
- They don’t solve for internal threats or compromised credentials of storage or backup admins.
- Recovery of large file volumes takes too long when you need to meet strict RPOs—and classifying that data for tiered recovery takes time and effort.
Air-gapped security strategies also can’t completely address the issues of reliability and speed—the two most important factors for successful recovery. What, then, is an all-around air-gapped solution that addresses simplicity, reliability, and speed?

Risk, Resilience, and Data Storage
Pure Storage CTO for the Americas, Andy Stone, sits down with the Wall Street Journal to share the latest in cyber resilience best practices.
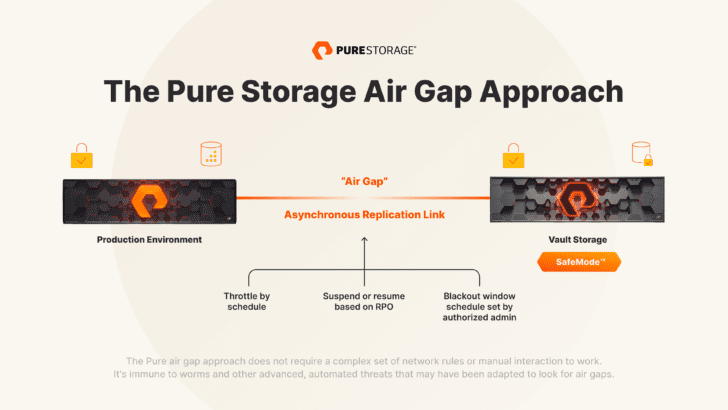
Pure’s Approach to Air Gap
Our modern take on the virtual air gap is a next-level implementation that offers all the benefits of an air-gapped data bunker, but with a key difference: it’s simpler AND faster.
Here’s how it works:
Pure Storage SafeMode™ feature is the key. SafeMode creates a secure enclave, from which snapshots cannot be deleted—whether it’s manually by a human or through a programmatic approach. Also, there is an additional human element on top of this. To manually eradicate snapshots, Pure’s solution requires real-time, interactive support, adding an extra layer of protection.
Then, there’s the simplicity. Built-in automation and preset timers deliver peace of mind without the extra work required to maintain programmatic or physical air gaps.
Finally, it’s sad but true: unless your data restores are fast enough to avoid major organization, reputational, and financial impact, all the work you’ve done around protection is worthless. Regardless of the platform or underlying technology (e.g., pointer-based snapshots or industry-leading throughput), Pure can deliver restore speeds that won’t keep your business waiting.
Part 2: Bunkered, Tiered Backup Architectures
- https://www.nytimes.com/2021/05/10/us/politics/pipeline-hack-darkside.html

*Pure products do not support WORM capabilities.