Update: Pure Storage® has ended support for EncryptReduce capability
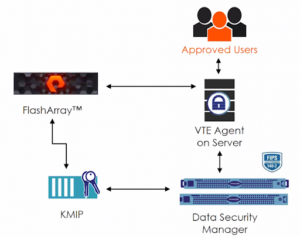
The Purity 5.3.7 operating environment for Pure Storage® FlashArray™ now supports EncryptReduce, which is compatible with Microsoft Windows operating systems. EncryptReduce uses Vormetric Transparent Encryption (VTE) from Thales to assist in securing block storage on FlashArray without losing the benefits of the always-on data deduplication technology in the array.
The Importance of Securing Data
In a world where the digitization of business is commonplace and data is more critical than ever to operate every day, preventing unauthorized access and use of data is possibly one of the most important things a business will do in its life span. You can secure access to data in multiple ways, including:
- Authentication control: This is a layer of security that verifies a user’s credentials and their access to them. Credentials can range from a simple passcode to username/password authentication and even biometric access.
- Access control: This layer of security ensures that the credentials provided through authentication control are on a trusted list before allowing access to secure objects. This form of data security typically comes in the form of an access control list (ACL) or object permissions.
- Data breach control (encryption): This type of security seeks to ensure that no matter where data is—in flight or at rest—it can’t be compromised or stolen. While no security system is impenetrable and compromise-proof, encrypting data provides an extra step towards making it incredibly difficult to do anything with the data if the systems are compromised.
Securing Data with FlashArray and Thales VTE
FlashArray, and the Purity Operating Environment in particular, has all the hallmarks of enterprise-class storage: authentication, access control, and encryption to secure data.
However, it doesn’t provide fully end-to-end data security. Data transmitted over the wire (in flight) is still insecure. If there’s a breach to the hosts’ operating systems, data can be copied off the filesystems.
One solution to this problem is to implement filesystem encryption or application (or database) encryption, but this limits data reduction (deduplication) capabilities. Data reduction and encryption are polar opposites. Data reduction identifies similar patterns in a data set to reduce the amount that needs to be processed. In contrast, encryption makes data as random as possible so that patterns can’t be identified.
To bridge the gap between these two disparate methods of processing data—and make them work together—you can use Thales VTE as an external key manager to encrypt block devices connected to hosts from a FlashArray device. When the encrypted data arrives on the FlashArray for storage, VTE provides a decryption key, delivering the following benefits:
- Encrypted data is transferred between the host and FlashArray.
- FlashArray can perform data reduction on the data.
- The VTE Data Security Manager (DSM) centralizes security and key management.
The VTE agent and DSM serve as the centralized gatekeeper allowing or denying access to data in the multiple forms it will take in its lifecycle. EncryptReduce works with the DSM to ensure that the FlashArray stores the most cost-effective form of the data in a secure and protected manner.
Implementing EncryptReduce on Microsoft Windows Server
While implementing EncryptReduce is easy, there are some restrictions. You can only use EncryptReduce with the following system types:
- Bare metal systems with volumes from FlashArray using iSCSI or Fibre Channel
- Hyper-V and VMware (RDMs and VVols) virtualized platforms for Microsoft Windows
- Windows Server versions 2012, 2012R2, 2016, and 2019
In addition, you’ll need to install the VTE agent for Windows on the system, set up the DSM, and register the VTE agent for Windows as a host.
In the implementation outlined below, I registered the FlashArray as a host on the same DSM cluster with KMIP registration allowed and communication enabled. A Windows Server system was also deployed with the Thales VTE Agent installed and configured to work with the DSM as a host supporting Efficient Storage.
Efficient storage is the functionality in the DSM that enables the exchange of keys to decrypt block storage data before it’s stored. Having a host system with efficient storage informs the DSM that the keys for that system’s encrypted volumes need to be given to the FlashArray.
The Microsoft Windows system with the VTE agent installed has a number of disks, but in this example only two volumes are encrypted. Use the following command in a powershell terminal to list the disks:
|
1 |
Voradmin esg list disk |

Only Disk1 and Disk2 need to be secured using VTE, so I execute the following command to ensure the disk can be used for efficient storage:
|
1 |
voradmin esg config new <device–name>=<label> |
Note that in this example, the device names are \Device\0000003c and \Device\0000003e.
Now the devices can be configured as guard points (volumes or filesystem access locations protected by VTE). Log in to the correct domain, go to the DSM, and navigate to Hosts. Select the GuardPoints tab and select Guard.
Before you can create the guard point, you’ll need to create a policy and provide the label specified in the “voradmin esg config new” command for the directory. In this example, the Protected Paths are VTE_Log and VTE_Data because they’re going to host a SQL Server database. Be sure to select Secure Start and Efficient Storage Device or IDT-Capable Device when creating the guard points. Once complete, the guard points should look something like this:
To verify everything in the OS is working as expected, execute the following command in a PowerShell window:

The status of the two devices we set up earlier should now appear as “guarded.” Now when you create a filesystem on the new devices, any data written to it will be encrypted.
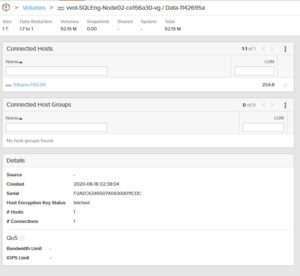
To verify if the key exchange between the DSM and FlashArray is working for these devices, simply look at them on the FlashArray:
Under Volumes, go to Volume Name. In this example, I’m using a vVol-based virtual system. Identify the volume that corresponds to the virtual machine’s virtual disks, and look at the Details section. If the DSM and FlashArray are communicating correctly, the Host Encryption Key Status should be “fetched.” This also means that FlashArray can perform data reduction on data being encrypted at the filesystem level.
Testing VTE for Microsoft Windows and EncryptReduce
To test EncryptReduce with a Microsoft Windows scenario, I created a SQL Server database, with the data files on one volume and the log files on another. I replicated this setup across three systems conforming to the following scenarios:
- No encryption whatsoever
- SQL Server Transparent Data Encryption
- SQL Server with EncryptReduce configured on the data and log volumes
Data Reduction
After adding 768GB of data to the database, the amount of data physically stored in each scenario was noticeably higher when using SQL Server Transparent data encryption than when using no encryption (insecure) or SQL Server with EncryptReduce. That’s almost a 3x difference!

Security
To test security, I created an additional policy to deal with access control. I used the guard point type, “Directory (Auto Guard),” which essentially limited access of the directory the SQL Server data and log files were on to a limited number of users. This not only secured the data in transit and at rest but also limited who had access to the SQL Server data volumes location and what they could do with it.
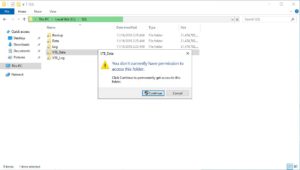
Here’s what a user would see if they don’t have access to the SQL Server data files:
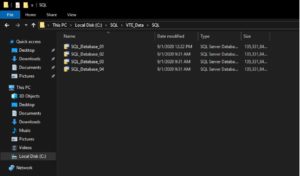
Here’s what a user would see when they do have access to the SQL server data files:
Note: You can establish additional security for Microsoft SQL Server by restricting login access to a specific user to ensure no one can browse the files and only the user running the database instance can interact with them.
Shutting Down the VTE DSM
In a simulation of someone trying to steal data, I shut down the DSM so the volumes couldn’t be accessed. The VTE agent prompted for a response challenge to access the volume. Once the DSM was available again, the prompt went away. However, if the volume is copied at the block level, a security key is required to gain access to the files.
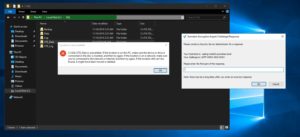
To expand upon this scenario in which a connectivity loss between the host systems and DSM is possible, there are three levels of security you can put in place to ensure a degree of business continuity:
- Pre-shared password: In the case of DSM network loss, you can enter a pre-shared password to regain access to the volume. This is the least secure but fastest resolution to ensure business operations continue.
- Challenge and response: This requires an active DSM but accounts for a scenario where network connectivity has been lost. A string of characters (challenge) is provided to the user to enter into the DSM, which then offers a response that is provided to the host. This offers a medium level of security as the user would need to work with the security team to do this process with a working DSM.
- No access: Access to the DSM is required before access to the data is granted. This is the most restrictive and secure method of storing sensitive data, but it also creates a risk to business continuity. A best practice in this scenario would be to build highly available DSM infrastructure with regular backups to ensure the least amount of downtime is experienced when any loss of connectivity occurs.
See SafeMode in Action
Take a closer look at how Pure protects your data
with built-in, immutable snapshots.
Final Thoughts
Thales Vormetric Transparent Data Encryption and Pure Storage FlashArray create a fantastic pair to protect data at various stages in its lifecycle and reduce costs through data-reduction capabilities. With the risks implicit in the ever-expanding growth of data and the capabilities technology enables, data security needs to be at the forefront of your plans when considering any form of digital transformation.
Learn how you can help fuel your company’s digital transformation plans with FlashArray.
Free Test Drive
Try FlashArray
Explore our unified block and file storage platform.