Summary
Threat Model Mentor GPT is an AI-powered tool created by Pure Storage that automates threat modeling and democratizes cybersecurity expertise.
In today’s hyper-competitive and fast-paced software development world, ensuring security is not a luxury—it’s a necessity. Yet, one of the most critical components of secure system design, threat modeling, remains out of reach for many teams due to its complexity and the specialized expertise it demands.
At Pure Storage, we envisioned using OpenAI’s custom GPT capability to create a “Threat Model Mentor GPT” to bridge this gap. Designed to simplify and democratize threat modeling, this AI-powered tool empowers teams to identify, assess, and mitigate security risks early in the development lifecycle. Here’s the story of how we built it and how it’s revolutionizing secure software development.
Understanding the Problem Space
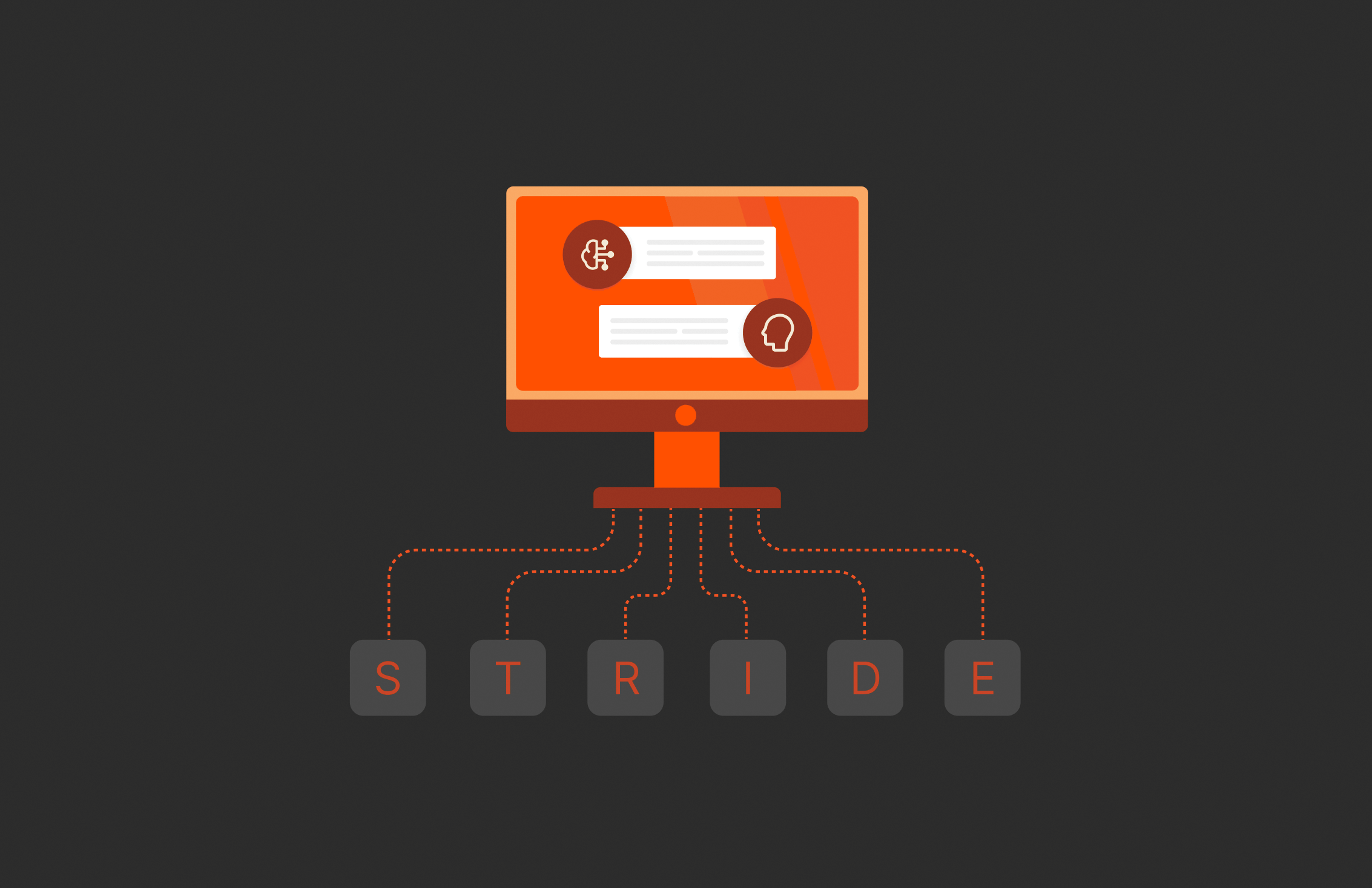
Threat modeling is a foundational step in designing secure systems, identifying vulnerabilities, and mitigating risks. Frameworks such as STRIDE provide systematic approaches to categorizing threats, but they come with significant challenges:
- Lack of expertise: Many teams lack access to security professionals skilled in threat modeling. This gap often leads to overlooked vulnerabilities, increasing the risk of data breaches and system compromises.
- Time constraints: Manual threat modeling is resource intensive and often delays project timelines, making it difficult to integrate into fast-moving development cycles.
- Integration difficulties: Aligning threat modeling with modern development workflows, including DevOps and agile practices, is a significant hurdle. This misalignment often leads to fragmented security efforts.
We saw an opportunity to build an AI-powered tool that automates threat modeling, provides actionable insights, and integrates seamlessly into existing workflows to bridge this gap.
Building Threat Model Mentor GPT
Our goal was ambitious yet clear: make threat modeling accessible to everyone. Whether you’re a seasoned security engineer or a developer new to the concept, Threat Model Mentor GPT aims to:
- Simplify the threat modeling process.
- Empower teams to identify and mitigate risks early in the development lifecycle.
- Integrate seamlessly into DevSecOps workflows.
To achieve this, we combined advanced AI capabilities with deep security knowledge.
1. Research and Knowledge Gathering
The foundation of Threat Model Mentor GPT lies in established security frameworks, such as:
- STRIDE: A methodology for identifying threats related to Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege.
- OWASP: A treasure trove of best practices for application security.
- Real-world use cases: We studied how threat modeling is applied to APIs, microservices, and cloud environments.
2. Designing the Architecture
We focused on breaking down systems into key components:
- Trust boundaries: Where control shifts between entities, like between a user and an API
- Entities and processes: Identifying actors and actions within the system
- Data flows: Mapping how data moves through the system
The bot was instructed to decompose these elements from user inputs, enabling precise threat identification.
3. Building Key Features
To provide maximum value, we developed features like:
- Interactive system decomposition: Users can describe their system using a wide range of artifacts such as design documents, block diagram images, source code, deployment scripts, etc., and the AI maps its components and threat boundaries.
- Automated STRIDE categorization: The AI applies STRIDE to identify threats for each component and boundary.
- Mitigation recommendations: Actionable advice tailored to the threats and system design.
4. Integration with Development Workflows
We ensured Threat Model Mentor GPT could integrate with modern tools like:
- CI/CD pipelines for continuous monitoring
- Project management platforms like JIRA for tracking threats and mitigations
Expected Output of Threat Model Mentor GPT
When teams use Threat Model Mentor GPT, they can expect a comprehensive and actionable output, including:
| Output Component | Description | Examples |
| 1. Decomposed System Model | Breaks down the system into trust boundaries, entities, data flows, and processes | Entities: User, database, APIData Flows: HTTP requests, database queriesTrust Boundaries: Between user and API, API and database |
| 2. STRIDE Categorization | Maps threats to system components based on STRIDE methodology | User Authentication: SpoofingData Transfer: TamperingAudit Logs: RepudiationStored Data: Information DisclosureService Availability: Denial of ServiceAccess Control: Elevation of Privilege |
| 3. Identified Threats | Lists specific threats relevant to the system design | – Credential theft via phishing- Unauthorized data modification via API tampering- Sensitive information exposure in logs |
| 4. Mitigation Strategies | Provides actionable recommendations to address identified threats | – Use MFA for authentication (Spoofing)- Enable HTTPS/TLS for secure data transfer (Tampering)- Implement logging with tamper-proof storage (Repudiation) |
| 5. Risk Prioritization | Ranks threats based on likelihood and potential impact | – High: API token leakage- Medium: Unauthorized database access- Low: Misconfigured logging system |
| 6. Suggested Controls | Recommends specific controls or tools to improve system security | – Enable AWS S3 versioning and Object Lock- Use IAM roles with least privilege access- Integrate with a WAF for API security |
| 7. Diagram Updates | Visual representation of the decomposed system with updated annotations for threats and mitigations | Updated diagram showing trust boundaries, secure data flows, and flagged components for further review |
| 8. Documentation Guidance | Provides detailed guidance for documenting the threat model | Template recommendations for capturing identified threats, mitigations, and rationales in design documents or wikis |
| 9. Actionable Next Steps | Lists prioritized actions for developers and security teams | – Implement rate limiting on APIs- Configure S3 bucket encryption- Schedule a follow-up review after deployment |
| 10. Educational Insights | Offers learning materials related to the identified threats and mitigations | Links to STRIDE methodology guides, OWASP resources, and best practices for secure API design |
Impact of Threat Model Mentor GPT
- System Decomposition
- Teams describe their system architecture, including entities, data flows, and trust boundaries.
- Threat Model Mentor GPT generates a visual model and maps potential threats.
- Threat Identification and Mitigation
- The tool categorizes threats based on STRIDE and suggests targeted mitigations.
- Teams receive recommendations such as enabling encryption, implementing rate limiting, or using tamper-proof logging.
- Prioritization and Planning
- Threats are ranked by likelihood and impact, helping teams focus on the most critical issues first.
- Teams can plan mitigation tasks, integrate them into their workflows (e.g., JIRA), and track progress.
- Continuous Integration
- By integrating into CI/CD pipelines, Threat Model Mentor GPT ensures that threat modeling remains a continuous process throughout development.
- Educational Value
- For teams new to threat modeling, the AI serves as both a tool and a teacher, explaining threats and mitigations in an easily digestible format.
Here’s how Threat Model Mentor GPT is already making a difference:
- A team designing a microservices-based application identified threats like API tampering and implemented mitigations within days, saving weeks of manual effort.
- Developers new to cybersecurity learned best practices through the tool’s interactive recommendations, fostering collaboration with security teams.
- By integrating into workflows, the tool transformed threat modeling from a bottleneck into an enabler of secure innovation.
Conclusion
Threat Model Mentor GPT represents a leap forward in making threat modeling accessible, efficient, and educational. By combining AI with proven methodologies, we’ve built a tool that democratizes cybersecurity expertise. Whether you’re a developer, security professional, or product manager, Threat Model Mentor GPT is here to help you design secure systems and stay ahead of evolving threats.
In subsequent blogs, we’ll present practical applications of the AI-assisted Threat Modeling process and technology.

ANALYST REPORT,