Ransomware has become a full-fledged, highly profitable business, generating billions of dollars for cybercriminals. But is paying the ransom the right thing to do for your organization if you’ve been attacked? The answer depends on who’s launching the attack, what they’re asking for, and how effective your data protection strategy is.

Safeguard Your Data—and Your Business
Ensure effortless business continuity and data recovery.
Escalating Global Efforts to Deter Cyberattacks
There’s an increasing push by governments to ban ransomware payments as a way to deter increasingly sophisticated cyberattackers. In October 2023, a 40-country alliance, led by the United States, committed to no longer pay ransoms demanded by cybercriminals. The task force, named International Counter Ransomware, has brought together EU countries, Brazil, Canada, Columbia, the UAE, Israel, Japan, and Nigeria, with the purpose of coordinating a global effort against ransomware networks. This includes drawing up a “blacklist” of suspicious digital wallets, rolling out AI-based technology to analyze blockchain, and identify criminal funds.
The US is also taking plenty of additional countermeasures when it comes to ransomware attacks, including recent sanctions on the Russia-based LockBit Ransomware Group. As one of the world’s most aggressive distributors of ransomware as a service (RaaS), the criminal organization was added to the Office of Foreign Assets Control (OFAC) sanctions list, making it illegal for US entities to pay ransoms to them or their affiliates.
While these efforts are valuable deterrents, the threat of ransomware continues for enterprises. Cybercriminals are notoriously ruthless and cunning, and the cost of a ransomware attack can be devastating.
Hackers May Post Your Sensitive Data Online
Hackers often exfiltrate valuable data during a cyberattack and threaten to post it online if you don’t pay up. This type of extortion-style attack, where data isn’t encrypted but a ransom is still demanded, is increasing. Hackers target the most valuable types of data (e.g., patient records, student records, and information about active law enforcement cases), and they know where to post it to do the most damage.
“You want to make attacking your organization as expensive, time-consuming, and difficult as possible for hackers. Your house should be harder to break into than your neighbors’. ”
In these situations, a company’s hands may be tied. Some attackers even threaten to be PR liaisons to the press—either informing the media of your breach or denying it occurred if you pay up. This move means it’s more important than ever to be proactive with data security.
The goal should always be to make attacking your organization as expensive, time-consuming, and difficult as possible for hackers. In other words, your house should be harder to break into than your neighbors’. (We’ll provide a few ways to do this below.)
You Could Face Prolonged Downtime—and the Costs That Come with It
If hackers take out your organization’s active directory, DNS, or other core services, or lock you out of your infrastructure entirely, you’re at their mercy without available recovery points. With this kind of attack, your employees can’t send emails, you can’t utilize VPN to access systems, and you can’t even log in. And, if you’re locked out of your email, the IT team would need to pick up the phone and make the call to sound the alarm—then go in-person to perform a manual restore.
If this goes on for more than 15 minutes—let alone days—the problems will quickly escalate.
For example, when Colonial Pipeline was hit by an attack, the result was massive supply chain disruptions that sent shock waves across the nation. But even internally, an outage can be disastrous. For the City of New Orleans, an attempted hack meant employees were locked out and couldn’t perform their work.
To mitigate this, organizations need available recovery points to get back up and running quickly. A plan to address this type of attack—say, with Rapid Restore and SafeMode™ snapshots, or with a ransomware recovery SLA (that includes a recovery plan)—can build recoverability into your data security strategy.
The Cost to Recover Could Be More than the Ransom
If you don’t pay up, it will be up to you to get systems back online and recover data from whatever backup and restore solutions you have. Without the right backup and recovery solution, this process can often cost more than paying the ransom. Deciding what to do frequently boils down to the speed of recovery and the complications that pile up.
When the city of Baltimore followed the FBI’s advice and refused to pay the $76K ransom, they were left dealing with the consequences of having zero access to their data. The city had to spend $10 million on recovery efforts, not including the $8M in lost revenue from a two-week outage of bill payment systems and real estate transactions.
What Happens If You Do Pay the Ransom?
So, let’s say you decide to pay. In a perfect world, your data would be restored in a blink, the hackers would go on their way, and you’d be back in business. But that’s rarely the case—and there are sometimes even implications if you do.
Paying the Ransom Won’t Guarantee You Get Your Data Back
It’s never a good idea to take a criminal at their word—especially when they’ve already got their end of the deal. On average, organizations that paid the ransom only had 65% of their encrypted data restored. For another 29%, more than half of their stolen data remains encrypted. This means it’s extremely unlikely you’ll get all of your data back, even if you pay.
Hackers’ Solutions May Be Too Slow
Even if you do pay up and get your data back—via a decryption key or tool provided by hackers, as in the Colonial Pipeline case—it could still take days. Sometimes these tools are slow. Other times, your forensics or recovery solutions may also take days or weeks once you’re back in.
To address this concern with speed and efficiency, Pure Storage has a ransomware recovery SLA in Evergreen//One™ storage-as-a-service to ship clean arrays next business day with an onsite engineer, and it’s complemented by our alliances with top backup and restore partners, such as Rubrik, Veeam, and Commvault.
It Could Encourage Them to Attack You Again
There’s another problem with paying the ransom. Authorities say paying the ransom can indicate vulnerabilities, making you an easy target for future attacks. Hackers may ask for even higher ransom amounts, and then add your organization’s name to a list of targets willing to pay. If you haven’t upgraded your backup and recovery solutions by then, you should plan on more ransomware attacks.
Bounce Back from an Attack with the first Ransomware Recovery SLA from Pure Storage
The price of ransomware almost always amounts to more than the cost of the ransom. Why? Whether you choose to pay or not, you could incur additional costs, such as shareholder lawsuits, regulatory compliance suits, increased insurance premiums, loss of intellectual property, and other investigations.
So, it just makes sense to make it as difficult as possible for hackers. The more it costs to attack you—in time and resources—the less attractive you are as a target. A few ways to do this include:
- Maintaining good data hygiene
- Event logging and analytics layers
- Application scanning and encryption key management
- Tabletop planning
- Testing recoverability
- End-user education to minimize the likelihood that compromised passwords and phishing scams create inroads for an attack
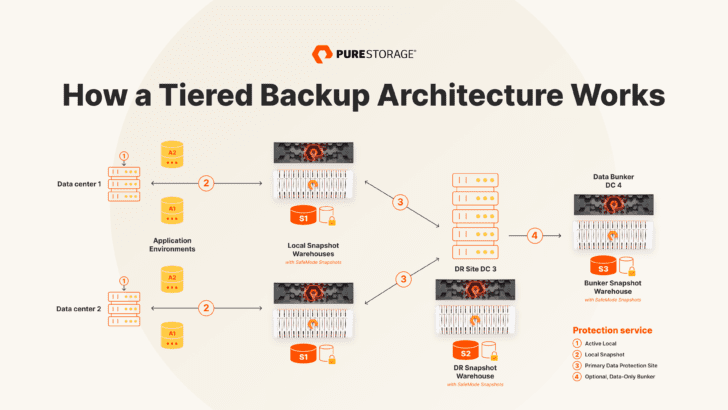
- A tiered backup architecture with data protection solutions that offer fast, reliable access to huge amounts of your data
- Virtual air gaps that keep mission-critical backups virtually (and physically) separate from production data
- Multifactor-authenticated, immutable snapshots. Ransomware attackers are more often going after your backups to really put you in a bind. Having multifactor-authenticated snapshots that can’t be edited or deleted, even by a rogue admin, take this bit of leverage off the table.
- Perform a data protection assessment comparing your configuration against leading practices and identifying areas where your data may be vulnerable across your entire fleet.
- Guarantee you have a clean environment to recover to with the Evergreen//One ransomware recovery SLA that includes a recovery plan, ships clean arrays next business day, and sends a professional services engineer onsite to rapidly bring your business back to normal operational level.
Prevention is certainly critical in combating ransomware—and you should deploy every tool and technology at your disposal to increase the cost of an attack. But if you’re worth enough, they will come after you—and prevention is nothing without a recovery solution for the “after” of an attack. There’s one thing that matters most in the after: recovery time. And it’s how Pure Storage solutions can help.

Written By:
Be Resilient
Test Drive FlashBlade with Built-in SafeMode Snapshots







